

RemediateSearchCVE Vulnerabilities withAI-Powered Remediation Guidance
Powerful Analysis Tools
Everything you need to secure your infrastructure
Bulk Analysis
Batch process CVEs instantly with EPSS & KEV status.
Patch Tuesday
Monthly security update highlights and critical patch analysis.
AI-Powered Remediation
Intelligent remediation guidance with tailored patch recommendations.
Export Options
Download reports in JSON, CSV, and Markdown formats.
JIRA Integration
Copy to JIRA format with action items and steps.
GitHub Issues
Create GitHub issues with formatted reports.
CVE Trends & Highlights
Affected devices do not properly enforce user authentication on specific API endpoints. This could facilitate an unauthenticated remote attacker to ci...
Cal.com is open-source scheduling software. From 3.1.6 to before 6.0.7, there is a vulnerability in a custom NextAuth JWT callback that allows attacke...
The vulnerability exists in BLUVOYIX due to the exposure of sensitive internal API documentation. An unauthenticated remote attacker could exploit thi...
A flaw in Node.js's permission model allows Unix Domain Socket (UDS) connections to bypass network restrictions when `--permission` is enabled. Even w...
Authentication Bypass by Primary Weakness, Weak Password Recovery Mechanism for Forgotten Password vulnerability in Birebirsoft Software and Technolog...
The vulnerability exists in BLUVOYIX due to improper authentication in the BLUVOYIX backend APIs. An unauthenticated remote attacker could exploit thi...
The vulnerability exists in BLUVOYIX due to improper authentication in the BLUVOYIX admin APIs. An unauthenticated remote attacker could exploit this ...
Successful exploitation of the SQL injection vulnerability could allow an unauthenticated remote attacker to execute arbitrary SQL commands on the vul...
TinyWeb is a web server (HTTP, HTTPS) written in Delphi for Win32. TinyWeb HTTP Server before version 1.98 is vulnerable to OS command injection via C...
Dokploy is a free, self-hostable Platform as a Service (PaaS). In versions prior to 0.26.6, a critical command injection vulnerability exists in Dokpl...
An attacker may gain unauthorized access to the host filesystem, potentially allowing them to read and modify system data.
Improper access control in Azure Resource Manager allows an authorized attacker to elevate privileges over a network.
Due to insufficient input validation in SAP S/4HANA Private Cloud and On-Premise (Financials General Ledger), an authenticated user could execute craf...
Vulnerability in the Oracle Agile Product Lifecycle Management for Process product of Oracle Supply Chain (component: Supplier Portal). The supporte...
The RegistrationMagic plugin for WordPress is vulnerable to Privilege Escalation in all versions up to, and including, 6.0.7.1. This is due to the 'ad...
The Integration Opvius AI for WooCommerce plugin for WordPress is vulnerable to Path Traversal in all versions up to, and including, 1.3.0. This is du...
Livewire Filemanager, commonly used in Laravel applications, contains LivewireFilemanagerComponent.php, which does not perform file type and MIME vali...
The Registration & Login with Mobile Phone Number for WooCommerce plugin for WordPress is vulnerable to Authentication Bypass in all versions up to, a...
The Advanced Custom Fields: Extended plugin for WordPress is vulnerable to Privilege Escalation in all versions up to, and including, 0.9.2.1. This is...
The Academy LMS – WordPress LMS Plugin for Complete eLearning Solution plugin for WordPress is vulnerable to privilege escalation via account takeover...
Latest from the Blog

The Weekly Cybersecurity Brief: February 6th, 2026
ShinyHunters escalated their campaign by publishing datasets from Harvard and UPenn, critical patches for MediaTek SoCs and Autodesk 3ds Max, plus this week's key trends in data extortion tactics.
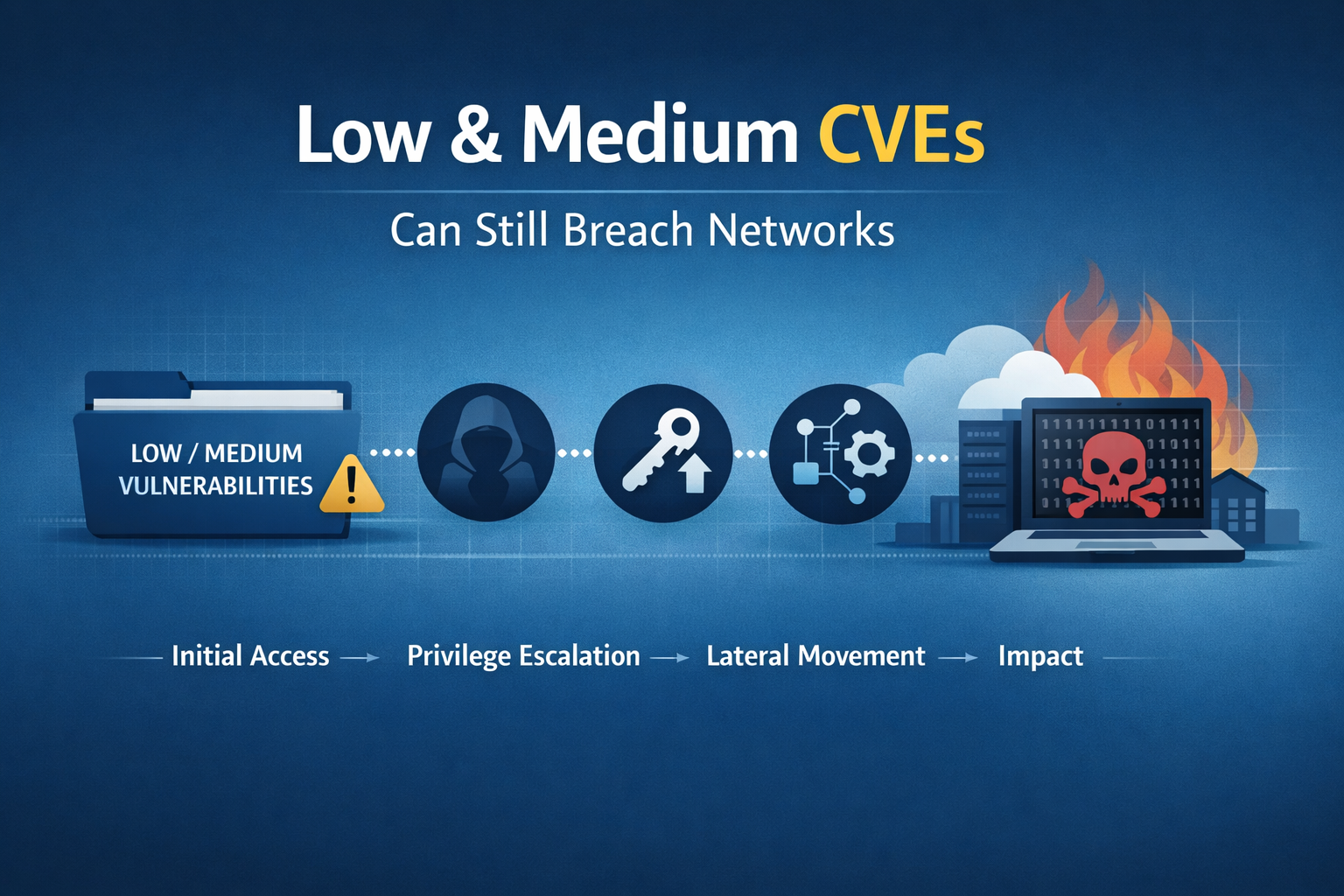
Why “Low” and “Medium” CVEs Still Breach Networks
In vulnerability management, severity ratings quietly shape behaviour. High and Critical CVEs trigger alerts, emergency patch windows, and executive attention. Low and Medium CVEs, by contrast, tend to sink into the backlog—scheduled, deferred, or ignored entirely. That complacency is increasingly misplaced.

The Weekly Cybersecurity Brief: January 30th, 2026
This week's cybersecurity brief covers Microsoft's emergency patch for the actively exploited Office zero-day CVE-2026-21509, critical vulnerabilities in Cisco UC products and Ivanti EPMM, plus the Nike ransomware breach exposing 1.4TB of data.